On-premises identity verification involves validating an individual’s identity within a physical location. This method ensures secure access and compliance with regulations.
On-premises identity verification is crucial for businesses needing secure access control and compliance. It involves using technology to verify identities within a physical location, enhancing security and reducing fraud risks. This method is especially important in industries like finance, healthcare, and government, where data protection is paramount.
Implementing effective identity verification systems helps organizations prevent unauthorized access and protects sensitive information. By utilizing advanced technologies, businesses can streamline their verification processes, ensuring efficiency and reliability. On-premises identity verification stands as a vital component in safeguarding assets and maintaining regulatory compliance.
Introduction To Identity Verification
In today’s world, identity verification is essential. It helps organizations confirm a person’s identity. This process is crucial for security and trust. On-premises identity verification is done within a company’s own infrastructure.
Companies use various methods to verify identities. These can include biometric checks, document scans, and more. Ensuring accurate identity verification prevents fraud and enhances safety.
Importance Of Identity Verification
Identity verification is vital for many reasons. It ensures that the person is who they claim to be. This process protects businesses from fraud and theft. It also helps in maintaining trust among customers.
In sectors like banking and healthcare, verifying identity is mandatory. It safeguards sensitive information and personal data.
- Prevents fraud
- Protects sensitive data
- Ensures regulatory compliance
Challenges In Verification
There are several challenges in identity verification. One major challenge is ensuring accuracy. Verifying identities can sometimes produce false positives or negatives.
Another challenge is integrating new technologies. Businesses must keep up with evolving threats and methods. This can be costly and time-consuming.
Privacy concerns also pose a challenge. Companies must handle personal information responsibly.
| Challenge | Details |
| Accuracy | Ensuring correct identity matches |
| Integration | Adopting new technologies |
| Privacy | Protecting personal data |
On-premises Vs. Cloud-based Solutions
Choosing between On-Premises and Cloud-Based Identity Verification solutions can be challenging. Each offers unique benefits. Understanding these differences helps make an informed decision for your business needs.
Benefits Of On-premises Verification
On-Premises verification provides greater control over your data. You can customize the system to fit specific needs. Security is managed internally, reducing external threats.
Here are some key benefits:
- Data Sovereignty: Keep data within your own servers.
- Customization: Tailor the system to meet specific requirements.
- Enhanced Security: Control over security protocols and measures.
- Reliability: No dependency on internet connectivity.
Comparing Cloud Solutions
Cloud-Based solutions offer different advantages. They are often cost-effective and scalable. With cloud solutions, you can access the system from anywhere.
Let’s compare On-Premises and Cloud-Based solutions:
| Aspect | On-Premises | Cloud-Based |
| Data Control | High | Medium |
| Customization | High | Low |
| Security | Enhanced | Shared |
| Scalability | Limited | High |
| Cost | High Initial | Subscription |
Key Components Of On-premises Identity Verification
On-premises identity verification ensures security and privacy. It requires specific hardware and software. These components work together to verify identities accurately.
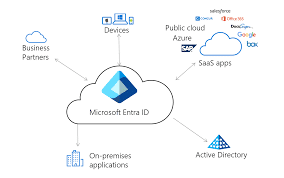
Hardware Requirements
On-premises verification starts with the right hardware. The key hardware components include:
- Biometric scanners: Fingerprint, face, or iris scanners.
- ID card readers: Devices to read smart cards or ID badges.
- Cameras: High-resolution cameras for face recognition.
- Servers: Secure servers to store and process data.
Choosing the right hardware ensures accurate and fast verification. Each piece plays a crucial role in the system.
Software Essentials
Software is the brain of the verification system. The key software components include:
- Identity management software: Manages user identities and credentials.
- Biometric matching algorithms: Compares biometric data with stored records.
- Database management systems: Stores and retrieves identity data securely.
- Integration tools: Connects the verification system with other IT systems.
Using the right software ensures that the system works smoothly. It provides accurate and reliable identity verification.
Both hardware and software are essential. They work together to provide a secure on-premises identity verification system.
Credit: learn.microsoft.com
Security Measures For On-premises Identity Verification
On-premises identity verification requires robust security measures. These measures ensure data protection and prevent unauthorized access. Let’s explore essential security aspects.
Data Encryption
Data encryption is vital. It protects sensitive information from cyber threats. Encryption converts data into unreadable formats. Only authorized users can access it.
There are two types of encryption:
- Symmetric encryption: Uses a single key for encryption and decryption.
- Asymmetric encryption: Uses a pair of keys, public and private.
Symmetric encryption is faster but less secure. Asymmetric encryption offers higher security. Choose the right encryption based on your needs.
Access Controls
Access controls limit who can access your data. They are crucial for protecting sensitive information. Access controls use various methods to ensure security.
Common methods include:
- Role-based access control (RBAC): Assigns permissions based on user roles.
- Multi-factor authentication (MFA): Requires multiple verification methods.
- Biometric authentication: Uses fingerprints or facial recognition.
RBAC is simple and effective. MFA adds an extra layer of security. Biometric authentication ensures only authorized users gain access.
Implementing these access controls protects against unauthorized access. It keeps your on-premises identity verification secure.
Compliance Standards
On-premises identity verification ensures businesses meet strict compliance standards. These standards safeguard data and protect user privacy. Understanding these standards is crucial for businesses.
Industry Regulations
Different industries have specific regulations. For example, healthcare follows HIPAA guidelines. Financial services adhere to FINRA and SEC regulations. Meeting these regulations is essential for avoiding penalties.
| Industry | Regulation |
| Healthcare | HIPAA |
| Financial Services | FINRA, SEC |
| Retail | PCI-DSS |
Meeting Legal Requirements
Businesses must also meet legal requirements. These requirements vary by country. For instance, GDPR applies in the EU. CCPA applies in California. Failing to comply can result in fines.
- GDPR in the European Union
- CCPA in California
- PIPEDA in Canada
Ensuring compliance involves regular audits and updates. Businesses should keep up with changing laws. This helps maintain compliance and avoid legal issues.
Implementation Strategies
Implementing On-Premises Identity Verification requires careful planning and execution. A robust strategy ensures security and compliance with industry standards. Below are some key steps and best practices for successful implementation.
Planning And Preparation
Start with a clear understanding of your security requirements. Assess the current infrastructure to identify gaps. Define the goals and objectives of the identity verification process.
- Create a detailed project plan.
- Assemble a dedicated team with specific roles.
- Set realistic timelines for each phase.
Ensure all stakeholders are aligned with the objectives. Conduct a risk assessment to identify potential threats. Develop a mitigation plan for each identified risk.
Deployment Best Practices
Follow best practices to ensure a smooth deployment process. Start with a pilot program to test the system in a controlled environment. This helps in identifying potential issues early.
- Choose the right technology: Select tools that meet your security needs.
- Integrate seamlessly: Ensure the new system integrates with existing infrastructure.
- Train your team: Provide comprehensive training to all users.
Monitor the deployment closely for any anomalies. Collect feedback from end-users to make necessary adjustments. Regularly update the system to address vulnerabilities.
Below is a quick comparison table to summarize key points:
| Aspect | Details |
| Planning | Define goals, assess infrastructure, create a detailed plan. |
| Preparation | Assemble team, conduct risk assessments, align stakeholders. |
| Deployment | Choose technology, integrate systems, train a team, monitor deployment. |
Common Pitfalls
Implementing on-premises identity verification can be challenging. Many businesses face common pitfalls during setup. These mistakes can lead to security risks and operational inefficiencies.
Avoiding Common Mistakes
Avoiding common mistakes can save time and resources. Here are some key points to consider:
- Incomplete Documentation: Ensure all steps are well-documented.
- Ignoring Updates: Always apply the latest security patches.
- Overlooking User Training: Train staff to recognize verification issues.
- Inadequate Backup Plans: Have a backup plan for system failures.
Troubleshooting Issues
Troubleshooting issues is crucial for smooth operations. Here are common issues and solutions:
| Issue | Solution |
| System Downtime: | Check server status and restart if necessary. |
| Verification Errors: | Recheck the user’s input data for accuracy. |
| Slow Performance: | Optimize database queries and server configurations. |
Future Trends Of On-Premises Identity Verification
The future trends in on-premises identity verification promise exciting advancements. As technology evolves, we can expect significant changes. Below are some key areas where these changes will occur.
Advancements In Technology
Technology is advancing at a rapid pace. This will impact identity verification. New methods will emerge. These include:
- Biometric Verification: Fingerprint and facial recognition are improving.
- AI and Machine Learning: These technologies will enhance accuracy.
- Blockchain: Secure and immutable records will be more common.
Predictions For The Future
The future holds many possibilities for on-premises identity verification. Here are some predictions:
- Increased Adoption: More businesses will use advanced verification methods.
- Integration with IoT: Devices will communicate to verify identities seamlessly.
- Enhanced User Experience: Verification processes will become faster and simpler.
The table below summarizes these predictions:
| Prediction | Details |
| Increased Adoption | More businesses will use advanced verification methods. |
| Integration with IoT | Devices will communicate to verify identities seamlessly. |
| Enhanced User Experience | Verification processes will become faster and simpler. |
Case Studies
Case studies provide real-world examples of on-premises identity verification. These examples show how businesses use this technology effectively. Let’s explore some successful implementations and lessons learned from these cases.
Successful Implementations
Many companies have adopted on-premises identity verification. Here are some examples:
| Company | Industry | Outcome |
| ABC Bank | Banking | Reduced fraud by 40% |
| XYZ Retail | Retail | Improved customer trust |
| 123 Healthcare | Healthcare | Protected patient data |
ABC Bank implemented on-premises identity verification. They saw a 40% reduction in fraud. This boosted their customer confidence.
XYZ Retail used this technology to verify customer identities. This improved trust and loyalty. They saw a significant rise in repeat customers.
123 Healthcare adopted on-premises identity verification. This ensured patient data was secure. They complied with strict healthcare regulations.
Lessons Learned
These case studies provide valuable lessons. Here are some key takeaways:
- Scalability: Ensure your system can grow with your business.
- User Training: Train staff to use the system efficiently.
- Regular Updates: Keep the system updated for security.
- Customer Support: Provide support for any issues.
Implementing on-premises identity verification can be challenging. Scalability is crucial. Your system should grow as your business grows.
User Training is essential. Staff must know how to use the system. This ensures smooth operation.
Regular updates keep the system secure. Regular Updates are vital to protect against new threats.
Provide Customer Support for any issues. This keeps the system running smoothly.
These lessons ensure successful implementation. They help businesses avoid common pitfalls.
Frequently Asked Questions
What Is The Identity Verification Process?
The identity verification process involves confirming a person’s identity using documents like a passport or driver’s license. It includes steps such as uploading documents, facial recognition, and sometimes answering security questions. This ensures secure access to services and prevents fraud.
What Does Identity Verification Require?
Identity verification requires a government-issued ID, a selfie, and sometimes additional documents. Ensure information matches for successful verification.
What Documents Can Be Used To Verify Identity?
Acceptable documents include passports, driver’s licenses, state ID cards, and military ID cards. Birth certificates and Social Security cards also work.
What Is An Identity Verification Provider?
An identity verification provider ensures the authenticity of a user’s identity. They use advanced technologies and databases to validate personal information. This helps prevent fraud and comply with regulations.
Conclusion
On-premises identity verification offers robust security and control. It ensures data privacy and meets regulatory standards. Businesses gain peace of mind with secure, in-house processes. Implementing this system can streamline operations and enhance trust. Embrace on-premises solutions to protect your organization and customer information effectively.


Real Estate I like the efforts you have put in this, regards for all the great content.