Video replay attacks can be prevented by using timestamping and encryption. Implementing two-factor authentication also enhances security.
Video replay attacks pose a significant threat to digital security. Cybercriminals exploit recorded video streams to gain unauthorized access or bypass security systems. Timestamping ensures each video frame has a unique, time-specific marker, making it difficult for attackers to reuse old footage.
Encryption secures the data, preventing unauthorized access or tampering. Combining these methods with two-factor authentication adds an extra security layer. This approach ensures that even if attackers gain access, they cannot easily exploit the data. Staying vigilant and continuously updating security protocols are essential for maintaining robust protection against video replay attacks.
Introduction To Video Replay Attacks
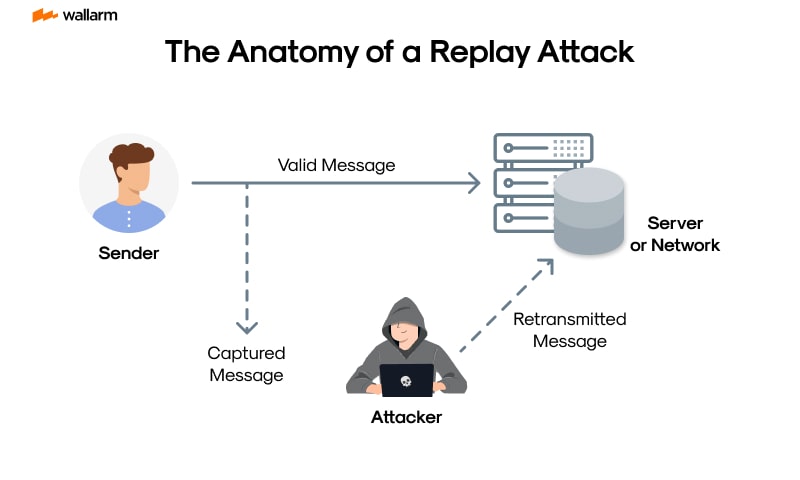
Video replay attacks are serious threats in the digital world. These attacks can bypass security measures. This section explains what video replay attacks are and their impact.
Definition And Examples
Video replay attacks involve capturing and reusing video footage. Attackers use old footage to gain unauthorized access.
- Example 1: An attacker reuses a video of a person unlocking a door.
- Example 2: Replaying a video of a person making a bank transaction.
These attacks trick security systems into believing the footage is real-time. This method can bypass many modern security measures.

Impact On Security
Video replay attacks pose a huge threat to security. They can cause unauthorized access and data breaches.
The impacts include:
- Loss of confidential information.
- Unauthorized access to secure areas.
- Financial losses due to fraud.
These attacks can damage an organization’s reputation. They also undermine trust in security systems.
Common Targets
Video replay attacks pose serious threats. Some targets are more attractive to attackers. Understanding these common targets helps in defending against such attacks.
Financial Institutions
Financial institutions are prime targets for video replay attacks. Attackers aim to access sensitive financial data. This includes bank accounts, credit card details, and personal information.
These institutions often use video surveillance for security. Attackers exploit these systems to gain unauthorized access. They replay recorded footage to bypass security checks.
Preventive measures for financial institutions:
- Implement multi-factor authentication to verify user identity.
- Use encryption for all video data.
- Regularly update security protocols to stay ahead of threats.
Online Retailers
Online retailers also face significant risks from video replay attacks. These businesses handle vast amounts of customer data. This includes payment information and personal details.
Attackers use replay attacks to manipulate transaction records. They can bypass security checks to make unauthorized purchases.
Preventive measures for online retailers:
- Monitor transaction patterns for unusual activities.
- Use secure payment gateways to protect customer data.
- Educate employees on recognizing and responding to security threats.
Detection Techniques
Video replay attacks pose serious threats to security systems. Detecting these attacks is crucial for maintaining system integrity. Various techniques help identify such malicious activities. Let’s explore some key methods for detecting video replay attacks.
Behavioral Analysis
Behavioral analysis involves observing and analyzing the behavior of video feeds. This method looks for unusual activities or inconsistencies. It helps in identifying potential replay attacks by comparing current behaviors with expected patterns.
- Motion Detection: Tracks unexpected movements in the video.
- Time-based Analysis: Checks for time discrepancies in the video feed.
- Contextual Clues: Analyzes the context to detect anomalies.
Pattern Recognition
Pattern recognition is another powerful technique. It uses algorithms to detect repetitive patterns. These patterns can indicate replay attacks if they do not match expected behaviors.
| Technique | Description |
| Algorithmic Matching | Compares video data to known patterns. |
| Machine Learning | Uses AI to learn and detect unusual patterns. |
| Frequency Analysis | Examines the frequency of events in the video. |
Authentication Methods
Authentication methods are essential for preventing video replay attacks. These methods ensure that the user is genuine and not using pre-recorded footage. Here, we will discuss two key authentication methods: Multi-Factor Authentication and Biometric Verification.
Multi-factor Authentication
Multi-Factor Authentication (MFA) requires users to provide multiple credentials. This can include something the user knows, something the user has, and something the user is. For instance, a password (knowledge), a smartphone (possession), and a fingerprint (inherence).
- Knowledge: This is something the user knows, like a password or PIN.
- Possession: This is something the user has, like a smartphone or security token.
- Inherence: This is something the user is, like a fingerprint or facial recognition.
MFA significantly improves security. It makes it hard for attackers to gain access using video replay attacks. Even if they have a video, they also need other factors.
Biometric Verification
Biometric Verification uses unique physical characteristics. These include fingerprints, facial recognition, and iris scans. Biometric data is hard to fake, making it a strong defense against video replay attacks.
| Biometric Type | Description |
| Fingerprint | Uses unique patterns on the user’s fingertip. |
| Facial Recognition | Uses the unique structure of the user’s face. |
| Iris Scan | Uses the unique patterns in the user’s iris. |
Biometric systems can detect live presence. This prevents attackers from using pre-recorded videos. They often check for natural movements, like blinking or smiling.
Encryption Strategies
Encryption is a key defense against video replay attacks. It ensures that videos are secure from unauthorized access and tampering. Here, we will explore two vital encryption strategies: End-to-End Encryption and Public Key Infrastructure.
End-to-end Encryption
End-to-End Encryption (E2EE) protects data in transit. It ensures that only the communicating users can read the messages. No one in between, including the service providers, can access the encrypted data.
- Messages are encrypted on the sender’s device.
- Only the recipient’s device can decrypt them.
- Prevents eavesdropping and tampering.
Popular apps like WhatsApp and Signal use E2EE. This makes it a trusted method for secure communication.
Public Key Infrastructure
Public Key Infrastructure (PKI) uses a pair of keys: a public key and a private key. The public key encrypts the data, and the private key decrypts it.
| Key Type | Function |
| Public Key | Encrypts data |
| Private Key | Decrypts data |
PKI ensures that even if someone intercepts the data, they can’t read it without the private key.
- Generate a key pair.
- Distribute the public key.
- Keep the private key secure.
PKI is widely used in HTTPS to secure web communications. It is a trusted method for protecting sensitive data.
Machine Learning Applications
Machine learning offers powerful tools to prevent video replay attacks. It uses data to detect patterns and make predictions. These applications enhance security and reduce the risk of fraud.
Anomaly Detection
Anomaly detection helps identify unusual activities in video feeds. Machine learning models analyze large volumes of data. They spot patterns that don’t fit the norm.
- Machine learning models can learn from past data.
- They identify anomalies in real-time.
- This helps in early detection of replay attacks.
By continuously monitoring the video streams, these models can flag suspicious activities. This makes it easier to take quick action.
Predictive Analytics
Predictive analytics forecasts potential threats before they occur. It uses historical data to predict future events.
- Collect data from various sources.
- Analyze past incidents of replay attacks.
- Train machine learning models on this data.
- Use the model to predict future threats.
This proactive approach helps in preparing for potential attacks. It reduces the element of surprise.
Both anomaly detection and predictive analytics make video replay attack prevention more effective. Using these machine learning applications enhances security measures significantly.
Best Practices For Businesses
Preventing video replay attacks is crucial. Businesses must adopt strong security measures. This ensures sensitive data remains protected. Below are some best practices to follow.
Regular Audits
Conduct regular audits of your security systems. Identify vulnerabilities and fix them promptly. Use automated tools for thorough checks.
- Schedule audits quarterly.
- Use updated tools for scanning.
- Review audit logs frequently.
Employee Training
Provide ongoing employee training on security practices. Educate staff on recognizing potential threats. This helps in early detection and prevention.
- Conduct monthly training sessions.
- Share latest security threats.
- Implement role-specific training modules.
Future Trends
Video replay attacks are a growing concern in digital security. Preventing these attacks requires innovative approaches. Let’s explore the future trends in video replay attacks prevention.
Ai-driven Security
Artificial Intelligence (AI) is transforming security measures. It can detect and prevent video replay attacks. AI uses machine learning to identify patterns. These patterns help in spotting anomalies quickly.
AI systems can analyze vast amounts of data. They learn from previous attacks and improve over time. This makes AI-driven security more effective. AI can also work in real-time. This offers immediate responses to potential threats.
A table can help summarize the benefits of AI-driven security:
| Benefits | Description |
| Real-Time Analysis | Identifies threats instantly |
| Pattern Recognition | Detects unusual activities |
| Continuous Learning | Improves with more data |
Blockchain Integration
Blockchain technology offers a secure way to store and verify data. It is decentralized and tamper-proof. This makes it ideal for preventing video replay attacks.
Blockchain can create a secure ledger of video files. Each video can have a unique digital signature. This ensures the video is genuine and unaltered. A blockchain ledger can also track the history of video files.
Here are some key points about blockchain integration:
- Secure and tamper-proof
- Decentralized ledger
- Unique digital signatures for videos
- Tracks history of video files
Combining AI and blockchain can offer robust security solutions. These technologies can work together to prevent video replay attacks effectively.
Case Studies
Understanding Video Replay Attacks Prevention requires analyzing real-world incidents. Studying these cases helps in grasping the severity and complexity of such attacks. This section will explore notable incidents and the lessons learned from them.
Notable Incidents
Several high-profile video replay attacks have occurred in recent years. Here are a few notable incidents:
| Incident | Description | Impact |
| Bank Heist | Attackers replayed video to bypass security cameras. | Millions in losses. |
| Corporate Espionage | Spies used replayed footage to steal trade secrets. | Loss of critical data. |
| Home Security Breach | Thieves replayed videos to enter a secure property. | Property theft. |
Lessons Learned
Each incident taught valuable lessons for preventing future attacks. Here are some key takeaways:
- Implement Timestamp Verification: Always verify the video timestamp to detect replays.
- Use Encrypted Channels: Ensure video data is encrypted during transmission.
- Deploy Multi-Layered Security: Combine video surveillance with other security measures.
- Regular Audits: Conduct frequent audits to identify potential vulnerabilities.
By analyzing these case studies, security professionals can better understand and mitigate video replay attacks.
Frequently Asked Questions
Does Vpn Prevent Replay Attacks?
A VPN can help prevent replay attacks by encrypting data. This makes it difficult for attackers to reuse intercepted information. Ensure your VPN uses robust encryption protocols for better protection.
How Does Tls Prevent Replay Attacks?
TLS prevents replay attacks by using unique session IDs and nonces. Nonces ensure each request is fresh. Session IDs maintain state. This combination stops attackers from reusing data packets.
How Do You Prevent Cookie Replay Attacks?
Use HTTPS, implement session expiration, and use unique, time-stamped tokens to prevent cookie replay attacks. Ensure secure cookie settings.
What Are The Tools For Replay Attack?
Tools for replay attacks include Wireshark, Cain & Abel, and Ettercap. These tools capture and replay network packets.
What Are Video Replay Attacks?
Video replay attacks involve recording and replaying videos to deceive security systems.
How Do Video Replay Attacks Work?
Attackers capture video feeds and replay them to bypass security systems.
Why Are Video Replay Attacks Dangerous?
They can compromise security by granting unauthorized access.
Conclusion
Preventing video replay attacks is crucial for online security. Implement strong authentication methods and regularly update your systems. Educate users about potential threats and best practices. By taking these steps, you can safeguard sensitive information and enhance trust. Stay vigilant and proactive to ensure a secure digital environment.


One Reply on “Video Replay Attacks Prevention: Essential Strategies and Tips”