Decentralized identity gives individuals control over their digital identities. It uses blockchain technology to enhance security and privacy.
Decentralized identity puts users in charge of their online information. This system uses blockchain to ensure data integrity. Traditional identity systems store data in central databases, which can be hacked. Decentralized identity stores data on a distributed ledger, making it secure.
Users can access services without sharing sensitive information. This enhances privacy and reduces the risk of identity theft. Businesses also benefit from reduced fraud and improved trust. As digital interactions grow, decentralized identity offers a safer, more private solution. It empowers people and improves online security. This technology is crucial for a safer digital future.
Introduction To Decentralized Identity
Decentralized Identity is a new way to manage digital identities. It gives users control over their personal data. This contrasts with centralized systems where data is stored on third-party servers.
Concept And Importance
Decentralized Identity means users own and control their data. It uses blockchain and cryptographic technology. This ensures security and privacy. Users can share their identity with others without intermediaries.
- Control over personal data
- Enhanced security
- Improved privacy
Businesses benefit from Decentralized Identity too. They can reduce risks related to data breaches. It also lowers costs for identity verification. This system is beneficial for everyone.
Historical Context
In the past, identity management was centralized. Companies like Google and Facebook held massive user data. Centralized systems posed many risks. Data breaches and privacy issues were common.
The concept of Decentralized Identity emerged with blockchain technology. Blockchain allows for secure and transparent transactions. This technology paved the way for new identity systems.
Decentralized Identity aims to solve problems with traditional identity management. It offers a safer and more private way to manage digital identities.
How Decentralized Identification Works
Decentralized Identity (DID) is a revolutionary approach to managing identities. It leverages blockchain technology and cryptographic principles. This system ensures privacy, security, and user control. Let’s explore how decentralized identity works.
Blockchain Technology
Blockchain is the foundation of decentralized identity. It records data on a distributed ledger. Each participant has a copy of this ledger. This ensures transparency and security.
In a blockchain, data is stored in blocks. Each block links to the previous one. This creates a chain of data blocks. Blockchain is immutable, meaning data cannot be altered once recorded. This property ensures the integrity of identity information.
Here’s a simple table explaining key blockchain properties:
| Property | Description |
| Decentralization | Data is distributed across many nodes. |
| Transparency | All participants can view the ledger. |
| Immutability | Data cannot be changed once recorded. |
Cryptographic Principles
Cryptography secures data in decentralized identity systems. It uses algorithms to encrypt data. Only authorized parties can decrypt and access the data.
Public and private keys are core elements of cryptographic systems. The public key is shared openly. The private key is kept secret by the owner. These keys work together to encrypt and decrypt data.
Here are the main cryptographic principles used in DID:
- Encryption:Transforming data into a secure format.
- Digital Signatures:Ensuring data authenticity and integrity.
- Hashing:Creating unique data fingerprints.
Cryptographic principles ensure that identity data is secure and trustworthy. This builds a robust foundation for decentralized identity.
Benefits Of Decentralized Identification
Decentralized Identity offers numerous advantages over traditional identity systems. This innovative approach allows individuals to control their own data. Below, we explore the key benefits of Decentralized Identity.
Enhanced Privacy
Decentralized Identity ensures enhanced privacy for users. Traditional systems store data on centralized servers. These servers are prone to breaches. In contrast, decentralized systems use blockchain technology. This means data is spread across multiple nodes.
This approach makes it harder for hackers to access sensitive information. Users have control over their data. They decide who can see their information. This reduces the risk of unauthorized access.
Improved Security
Decentralized Identity provides improved security features. Centralized systems are often targets for cyberattacks. One breach can expose millions of records. Decentralized systems distribute data across a network.
This distribution makes it more difficult for attackers. Each node holds only a piece of the data. To access complete information, hackers need to compromise multiple nodes. This added layer of security is crucial.
Below is a comparison table of traditional and decentralized identity systems:
| Feature | Traditional Identity | Decentralized Identity |
| Data Storage | Centralized Servers | Distributed Nodes |
| Privacy Control | Limited User Control | User Controlled |
| Security Level | Prone to Breaches | Highly Secure |
Decentralized Identity brings a new era of data protection. Users have better privacy and security. The system’s design ensures safety and trust.
Real-world Applications
Decentralized Identity (DID) is transforming various sectors by offering secure and private digital identities. Below, explore how DID impacts real-world applications in financial services and healthcare.
Financial Services
Decentralized Identity revolutionizes financial services by enhancing security and reducing fraud. Traditional identity systems often fall prey to breaches and identity theft. DID provides a safer alternative.
With DID, users control their personal data. Financial institutions can verify identities without accessing sensitive information. This minimizes risks and builds trust between parties.
Benefits of DID in Financial Services:
- Improved security
- Reduced fraud
- Enhanced privacy
- Faster verification processes
Smart contracts can automate transactions, ensuring transparency and efficiency. DID supports seamless cross-border payments and compliance with regulations.
Healthcare
Healthcare systems benefit significantly from Decentralized Identity. Patients gain control over their medical records, enhancing privacy and data security.
Doctors and hospitals can access verified patient information quickly, improving treatment accuracy and reducing errors. DID ensures that only authorized parties access sensitive data.
Advantages of DID in Healthcare:
- Enhanced patient privacy
- Accurate and efficient medical records
- Better data security
- Streamlined patient onboarding
A decentralized approach supports telemedicine by verifying identities remotely. This reduces the need for physical interactions, making healthcare more accessible.
Challenges And Limitations
Decentralized Identity (DID) brings many benefits. Yet, it faces several challenges and limitations. Understanding these hurdles is essential for its adoption and growth. This section will explore the major issues, focusing on Scalability Issues and Regulatory Hurdles.
Scalability Issues
DID systems struggle with scalability. As more users join, the network slows down. This can result in delays and inefficiencies.
For instance, the process of verifying identities can become time-consuming. This is problematic for industries needing quick and reliable identity checks.
| Issue | Impact |
| Network Congestion | Slow verification processes |
| High Transaction Costs | Increased operational expenses |
| Resource Intensive | Requires significant computational power |
Regulatory Hurdles
DID systems must comply with various regulations. These can vary greatly across countries and regions. Navigating these regulations is complex and time-consuming.
For example, data protection laws like GDPR in Europe impose strict rules. These rules can limit how decentralized identities are managed and stored.
- Compliance Costs:High costs associated with meeting regulatory requirements.
- Legal Uncertainty:Ambiguity in laws can lead to potential legal issues.
- Cross-Border Challenges:Different laws in different regions complicate implementation.
These hurdles can deter organizations from adopting DID solutions. They need clear guidelines and frameworks to operate effectively.
Key Players In Decentralized Identification
Decentralized identity represents a paradigm shift in how we manage and secure our personal information. Several key players are driving innovation in this space, including leading companies and innovative startups. Understanding who these players are helps us appreciate the ongoing evolution in identity management.
Leading Companies
Several established companies are pioneering in the decentralized identity sector. They leverage their resources to develop robust, scalable solutions.
- Microsoft:Microsoft is at the forefront with its decentralized identity solutions. Their project, ION, is built on the Bitcoin blockchain.
- IBM:IBM is integrating decentralized identity into its blockchain offerings. Their solution aims to enhance security and privacy.
- Hyperledger:Hyperledger, an open-source collaborative effort, provides tools and frameworks. They support decentralized identity initiatives worldwide.
Innovative Startups
Startups play a crucial role in driving innovation. Their fresh perspectives and agile approaches fuel rapid development in decentralized identity.
- uPort:uPort creates self-sovereign identity systems. These systems give users control over their data.
- Sovrin:Sovrin Foundation offers a decentralized global public network. Their aim is to provide a trusted identity for everyone.
- Evernym:Evernym develops technology for self-sovereign identity. Their solutions are widely adopted in various sectors.
These key players are shaping the future of decentralized identity. Their contributions are vital in creating secure, user-centric identity solutions.
Future Trends
The future of Decentralized Identity is bright and promising. With rapid technological advancements and evolving policy frameworks, the landscape is set to transform significantly. Let’s explore the key trends shaping this exciting future.
Technological Advancements
Technological advancements are crucial for the growth of Decentralized Identity. New technologies are being developed to enhance security, scalability, and user experience.
- Blockchain Technology:Blockchain ensures secure and tamper-proof identity management.
- Zero-Knowledge Proofs:These allow users to prove identity without revealing personal data.
- Self-Sovereign Identity (SSI):SSI gives users full control over their digital identities.
These advancements aim to provide better privacy and data security for users worldwide.
Policy Developments
Policy developments play a vital role in the adoption of Decentralized Identity. Governments and organizations are working on regulations to ensure safe and ethical use of this technology.
| Region | Policy |
| European Union | GDPR ensures data protection and privacy. |
| United States | CCPA provides rights over personal data for California residents. |
These policies aim to protect user data and promote trust in Decentralized Identity systems.
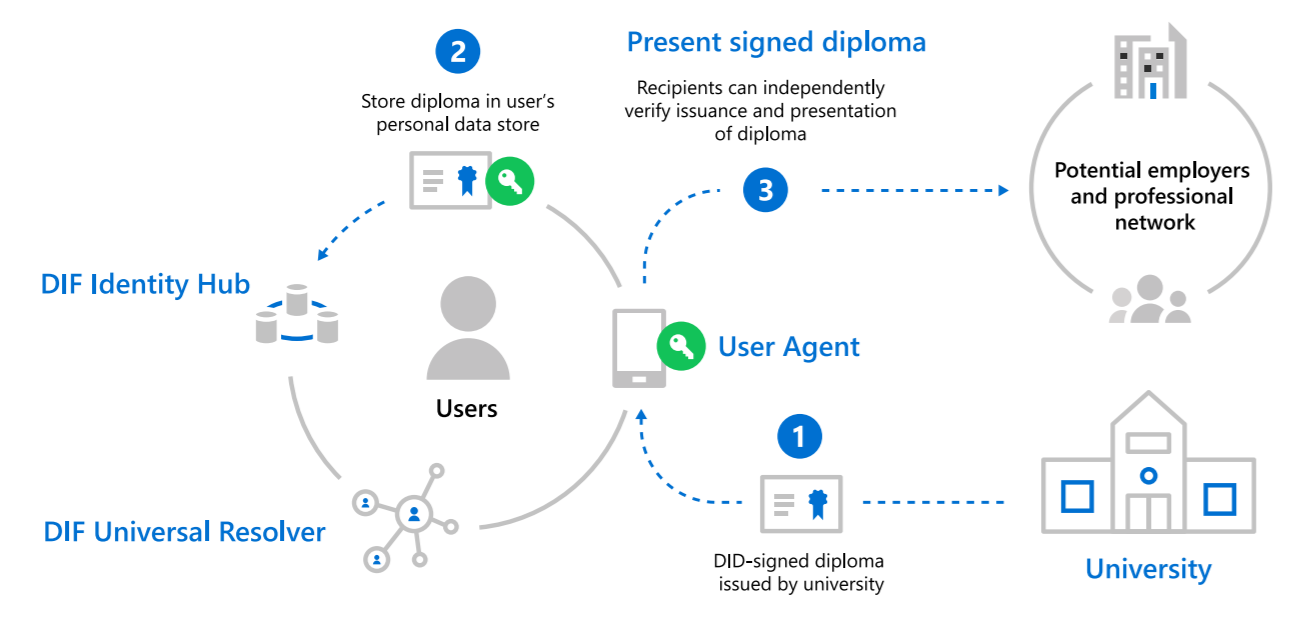
Steps To Adopt Decentralized Identification
Adopting Decentralized Identity is a transformative step for both individuals and organizations. It offers enhanced security, privacy, and user control over personal data. This section outlines the essential steps to implement decentralized identity effectively.
Implementation Strategies
To successfully adopt decentralized identity, follow these implementation strategies:
- Assess Current Infrastructure:Evaluate your existing systems and identify areas for integration with decentralized identity solutions.
- Select Suitable Technology:Choose the right blockchain technology or decentralized network that meets your security and scalability needs.
- Develop Integration Plan:Create a detailed plan outlining how decentralized identity will be integrated into your current workflows.
- Train Your Team:Educate your staff about decentralized identity and its benefits to ensure smooth implementation.
- Start with a Pilot:Begin with a small-scale pilot project to test the technology and processes before full deployment.
Best Practices
To maximize the benefits of decentralized identity, follow these best practices:
- Prioritize Security:Implement robust security measures to protect user data and prevent unauthorized access.
- Ensure Interoperability:Choose solutions that are compatible with other systems and standards to facilitate seamless integration.
- User-Centric Design:Focus on user-friendly interfaces and processes to enhance user adoption and satisfaction.
- Regular Audits:Conduct regular security audits to identify and address potential vulnerabilities.
- Stay Updated:Keep abreast of the latest advancements and trends in decentralized identity technology.
Adopting decentralized identity involves careful planning and execution. By following these steps and best practices, you can ensure a successful transition to a more secure and user-centric identity management system.

Frequently Asked Questions
What Is Decentralized Identification?
Decentralized identity is a system where individuals control their own digital identities. It eliminates the need for central authorities. This provides greater privacy and security.
How Does Decentralized Identification Work?
Decentralized identity uses blockchain and cryptographic technologies. It allows users to manage their credentials independently. Verification is done through a peer-to-peer network.
Why Is Decentralized Identification Important?
Decentralized identity enhances privacy and security. It reduces reliance on central authorities. Users have more control over their personal data.
What Are The Benefits Of Decentralized Identification?
Decentralized identity offers better security and privacy. It reduces identity theft risks. Users have control over their personal information.
Conclusion
Decentralized identity offers security and privacy. It empowers users to control their data. This technology can reduce fraud and enhance trust. Embracing decentralized identity could transform digital interactions. Stay informed and consider its potential benefits.


One Reply on “What Is Decentralized Identity: Digital Privacy and Security in 2025”