Identity Orchestration is a crucial concept in modern security. It helps manage and automate identity processes.
In today’s digital world, businesses deal with multiple identity systems. Managing these systems can be complex and time-consuming. Identity Orchestration simplifies this process. It automates tasks like user authentication, authorization, and provisioning. This ensures seamless and secure access across various platforms.
It also reduces the risk of security breaches. By using Identity Orchestration, organizations can enhance their security posture. They can also improve user experience. This blog will explore the benefits and strategies of Identity Orchestration. We will discuss how it can help your business stay secure and efficient.
Introduction To Identity Orchestration
In today’s digital age, managing identities is more crucial than ever. Organizations need a way to streamline identity management processes. This is where Identity Orchestration comes in. It offers a comprehensive solution to handle user identities efficiently.
What Is Identity Orchestration?
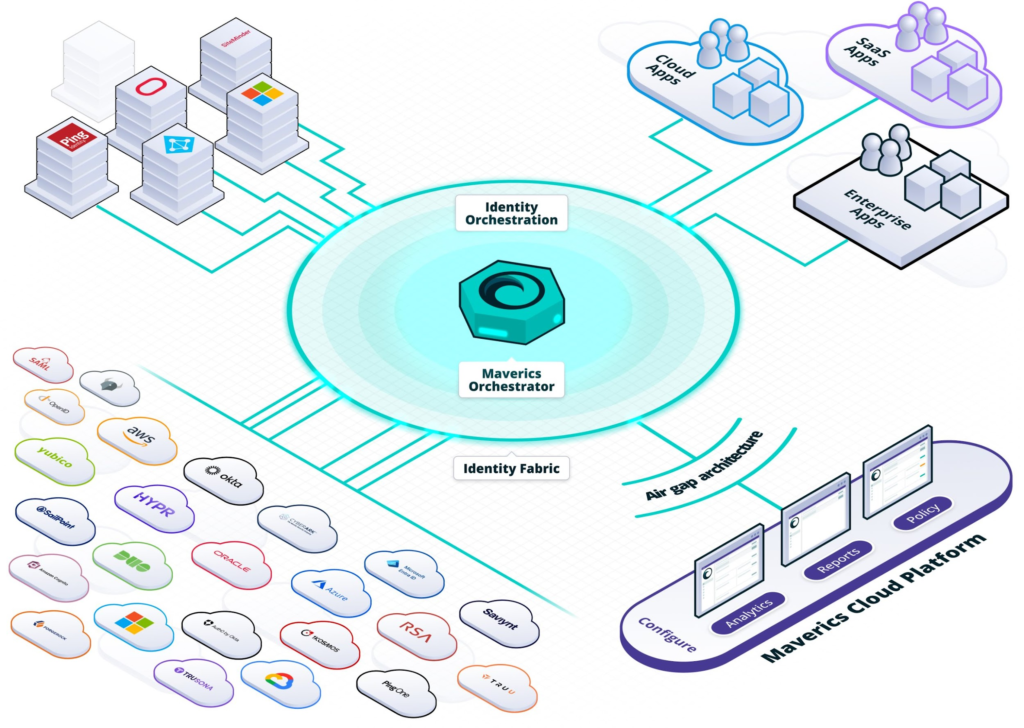
Identity Orchestration is a system that automates identity management. It integrates various identity services into a unified platform. This includes authentication, authorization, and user management.
- Authentication: Verifies user identity.
- Authorization: Grants access based on identity.
- User Management: Handles user data and permissions.
With Identity Orchestration, organizations can ensure seamless user experiences. It also reduces the complexity of managing multiple identity systems.
Importance In Digital Security
Digital security relies heavily on identity management. Effective Identity Orchestration enhances security by ensuring only authorized users gain access.
Here are some key benefits:
- Enhanced Security:Prevents unauthorized access.
- Streamlined Processes:Reduces manual intervention.
- Scalability:Adapts to growing user bases.
Furthermore, it helps in complying with regulatory standards. This is crucial for organizations handling sensitive data.
| Benefit | Description |
| Enhanced Security | Protects against unauthorized access and breaches. |
| Streamlined Processes | Automates identity management tasks. |
| Scalability | Supports large numbers of users efficiently. |
In summary, Identity Orchestration is vital for modern digital security. It ensures that organizations can manage identities effectively and securely.
Key Components
Identity Orchestration is a complex system with several key components. Understanding these components is crucial for managing identities efficiently. Below, we explore two vital elements: Authentication Methods and Authorization Protocols.
Authentication Methods
Authentication methods verify the identity of a user. Various techniques ensure the security and reliability of this process. Here are some common methods:
- Passwords: The most basic form of authentication. Users enter a secret word to gain access.
- Biometrics: Uses physical characteristics like fingerprints or facial recognition.
- Multi-Factor Authentication (MFA): Combines two or more methods for enhanced security.
- Tokens: Physical devices or software that generate a unique code.
- Single Sign-On (SSO): One set of credentials to access multiple applications.
Authorization Protocols
Authorization protocols determine what actions a user can perform. These protocols ensure only authorized users can access certain resources. Key protocols include:
- OAuth: An open standard for access delegation. It allows secure access without sharing credentials.
- SAML: Security Assertion Markup Language. It exchanges authentication and authorization data between parties.
- OpenID Connect: A simple identity layer on top of OAuth 2.0. It verifies the end user’s identity.
- RBAC: Role-Based Access Control. It assigns permissions based on the user’s role within an organization.
- ABAC: Attribute-Based Access Control. It grants access based on attributes and policies.
Benefits Of Identity Orchestration
Identity Orchestration offers many advantages for businesses today. It streamlines the management of user identities, ensuring both security and user satisfaction. Below, we explore some key benefits of Identity Orchestration.
Enhanced Security
Identity Orchestration improves security by centralizing and automating identity management. This reduces human error and ensures consistent application of security policies. Automated processes help detect and respond to threats faster. This minimizes the risk of data breaches.
- Centralized Management:All identities managed from one place.
- Automated Security Policies:Consistent enforcement of rules.
- Rapid Threat Response:Quick detection and action on threats.
Improved User Experience
Users enjoy a seamless experience with Identity Orchestration. It simplifies access to resources by using single sign-on (SSO). Users only need to remember one set of credentials. This reduces frustration and increases productivity.
- Single Sign-On (SSO):One login for multiple applications.
- Reduced Password Fatigue:Fewer passwords to remember.
- Increased Productivity:Less time spent on logging in.
Identity Orchestration also supports multi-factor authentication (MFA). This adds an extra layer of security without complicating the user experience. Users can verify their identity through multiple methods, such as SMS or email.
- Multi-Factor Authentication (MFA):Extra security with ease.
- Various Verification Methods:Options like SMS or email.
Challenges And Solutions
Identity Orchestration is critical in managing user identities across various systems. This process faces several challenges, but effective solutions can mitigate these issues.
Common Challenges
Implementing Identity Orchestration can be complex. Here are some common challenges:
- Integration Complexity:Connecting multiple identity systems is not simple.
- Scalability Issues:Systems must handle large user bases efficiently.
- Security Risks:Protecting user data is paramount.
- User Experience:Ensuring a seamless user experience is challenging.
Effective Solutions
Addressing these challenges requires a strategic approach. Here are some effective solutions:
| Challenge | Solution |
| Integration Complexity | Use standard protocols like SAML and OAuth. |
| Scalability Issues | Implement cloud-based solutions for better scalability. |
| Security Risks | Adopt multi-factor authentication (MFA) for added security. |
| User Experience | Ensure single sign-on (SSO) for a smoother experience. |
By addressing these challenges with effective solutions, organizations can improve their Identity Orchestration processes.
Implementing Identity Orchestration
Identity Orchestration involves the coordination of multiple identity and access management (IAM) processes. It aims to create a seamless and secure user experience. This process ensures that different IAM systems work together efficiently. Now, let’s dive into the steps and best practices for implementing Identity Orchestration.
Steps To Implementation
Implementing Identity Orchestration follows several critical steps. Follow these steps to ensure a smooth integration:
- Assess Your Current System:Identify existing IAM processes and systems.
- Define Objectives:Set clear goals for what you want to achieve.
- Choose the Right Tools:Select tools that fit your objectives and integrate well.
- Design the Workflow:Plan how different IAM processes will interact.
- Implement in Phases:Start with a pilot phase, then scale up.
- Monitor and Optimize:Continuously track performance and make improvements.
Best Practices
To ensure successful Identity Orchestration, consider these best practices:
- Prioritize Security:Ensure all IAM processes are secure and compliant.
- Maintain Flexibility:Your system should adapt to future changes and needs.
- Enable Single Sign-On (SSO):Simplify user access with SSO integration.
- Ensure Interoperability:Different IAM systems should work well together.
- Focus on User Experience:The process should be seamless for end-users.
- Regular Audits:Conduct audits to identify and fix vulnerabilities.
Following these steps and best practices will help ensure a smooth and efficient implementation of Identity Orchestration. This will lead to a more secure and user-friendly IAM environment.
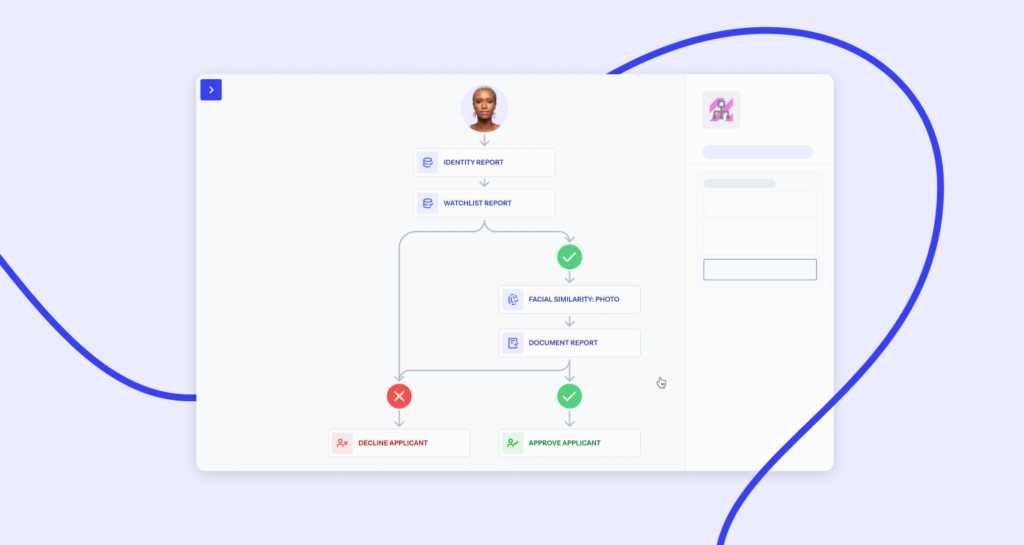
Case Studies
Identity Orchestration has transformed how businesses manage digital identities. This section examines real-world case studies to showcase its impact. We delve into successful implementations and the lessons learned from these experiences.
Successful Implementations
Many companies have benefited from Identity Orchestration. Here are a few examples:
- TechCorp: A leading tech company streamlined user authentication. They reduced login times by 40%.
- HealthFirst: A healthcare provider enhanced patient data security. They saw a 50% drop in data breaches.
- EduLearn: An e-learning platform improved user experience. They increased student engagement by 30%.
Let’s look at these in more detail:
| Company | Challenge | Solution | Outcome |
| TechCorp | Slow authentication process | Implemented Identity Orchestration | 40% faster logins |
| HealthFirst | Data breaches | Enhanced security measures | 50% fewer breaches |
| EduLearn | Poor user experience | Integrated seamless authentication | 30% higher engagement |
Lessons Learned
From these implementations, several key lessons emerged:
- Customization is key: Tailor solutions to fit specific needs.
- Continuous monitoring: Regular checks ensure optimal performance.
- Employee training: Educate staff on new systems for smooth transitions.
Successful Identity Orchestration requires a strategic approach. Consider these lessons for effective implementation.
Future Trends
The landscape of Identity Orchestration is ever-changing. Understanding future trends can help organizations stay ahead. Here, we will explore emerging technologies and predicted developments in this field. These insights can help shape strategies for identity management.
Emerging Technologies
Several technologies are set to transform Identity Orchestration. These innovations promise to enhance security and efficiency.
- Artificial Intelligence (AI): AI can predict and mitigate security threats. It also helps in automating identity verification processes.
- Blockchain: Blockchain ensures data integrity and transparency. It can decentralize identity management, making it more secure.
- Biometrics: Biometric authentication is becoming more common. It provides a higher level of security than traditional passwords.
Predicted Developments
Future developments in Identity Orchestration will likely focus on improving user experience and security. Here are some predictions:
- Zero Trust Security: This model assumes that threats can come from anywhere. It requires strict verification for every user and device.
- Privacy-Enhancing Technologies (PETs): PETs will help protect user data. They ensure that data is shared only when necessary.
- Automated Compliance: Compliance with regulations will become automated. This will reduce the burden on organizations and improve accuracy.
These trends highlight the need for continuous adaptation. Staying informed about these changes is crucial for effective identity management.
Frequently Asked Questions
What Is Identity Orchestration?
Identity orchestration is the process of managing and automating identity verification.
Why Is Identity Orchestration Important?
It improves security, reduces fraud, and enhances user experience.
How Does Identity Orchestration Work?
It integrates various identity systems and tools into a single workflow.
What Are The Benefits Of Identity Orchestration?
Better security, streamlined processes, and improved user experience.
Who Can Use Identity Orchestration?
Businesses, organizations, and institutions needing secure identity management.
Is Identity Orchestration Secure?
Yes, it uses advanced technologies to protect user identities.
What Tools Are Used In Identity Orchestration?
Identity verification software, authentication tools, and security protocols.
Can Identity Orchestration Be Customized?
Yes, it can be tailored to meet specific business needs.
Conclusion
Identity Orchestration simplifies complex security processes. It ensures smooth, safe user experiences. Businesses benefit from streamlined authentication and improved efficiency. Users enjoy quick access without compromising security. Embrace this approach for better digital interactions. Your organization’s security and user satisfaction will thank you.















