Individual verification is a key process used to confirm the identity of a single person. This practice is essential in various fields, such as finance, healthcare, and online services.
In an increasingly digital world, ensuring that individuals are who they claim to be is more important than ever. Individual verification helps prevent fraud and protect sensitive information. Organizations use different methods to verify identities, from basic document checks to advanced biometric systems like Face Recognition.
The goal is to create a secure environment for transactions and interactions. By understanding individual verification, you can appreciate its role in safeguarding personal data and enhancing trust in various services. This blog post will explore the importance, methods, and benefits of individual verification in our daily lives.
The Importance Of Individual Verification
Individual verification is crucial in today’s digital world. It helps protect personal information. Identity theft is rising. Without verification, individuals face significant risks. Companies also lose trust and revenue.
Reliable verification methods, such as Face Recognition, are essential. They ensure that only the right people access sensitive data. They ensure that only the right people access sensitive data. This process builds trust between users and organizations. Understanding the importance of individual verification is vital.
The Rise Of Online Identity Theft
Online identity theft is a growing concern. Criminals use technology to steal personal information. They target individuals and businesses alike. Phishing scams and data breaches are common tactics.
With more people online, the risk increases. Cybercriminals exploit weak verification processes. Many victims suffer financial loss and emotional distress. Protecting oneself from these threats is necessary.
Consequences Of Inadequate Verification
Inadequate verification can lead to severe consequences. Identity theft can ruin a person’s credit score. It can take years to recover from such damage. Financial losses can also burden individuals and businesses.
Companies face legal issues if they fail to verify properly. They risk losing customers and reputation. Trust is hard to regain once lost. Strong verification processes are essential to avoid these pitfalls.
Key Methods Of Individual Verification
Individual verification is essential for confirming a person’s identity. Various methods exist to ensure accuracy and security. Here are some key methods used in individual verification.
Knowledge-based Authentication
Knowledge-based authentication relies on information only the individual knows. This often includes personal questions. Examples are names of pets or favorite places. It is simple and easy for users. However, it can be vulnerable to guesswork and social engineering.
Two-factor Authentication
Two-factor authentication adds an extra layer of security. Users must provide two forms of identity. This often combines something they know and something they have. For example, a password plus a code sent to their phone. This method greatly reduces the risk of unauthorized access.
Credit Bureau-based Checks
Credit bureau-based checks use information from credit agencies. These checks verify identity through credit history. They can confirm a person’s name, address, and Social Security number. This method is reliable but may require consent from the individual.
Database Methods
Database methods involve cross-referencing information with various databases. Organizations can match details against government records. This method ensures accuracy and helps reduce fraud. It is often used in financial institutions and government services.
Biometric Solutions In Individual Verification
Biometric solutions, including Face Recognition, enhance individual verification by using unique physical traits. This method ensures accurate identification through fingerprints, facial recognition, or iris scans. This method ensures accurate identification through fingerprints, facial recognition, or iris scans. Such technology provides a secure way to confirm identities, making processes safer and more efficient for both individuals and organizations.
Biometric solutions play a crucial role in individual verification, providing a level of security and convenience that traditional methods often lack. These technologies rely on unique biological traits, making it significantly harder for unauthorized users to gain access. As we move further into a digital age, understanding how these biometric solutions work can help you appreciate their importance in safeguarding your identity.
Fingerprint Recognition
Fingerprint recognition is one of the most common biometric methods used today. Your fingerprints are unique, meaning no two individuals share the same patterns. This makes them an excellent tool for verifying identity. Many smartphones now use fingerprint sensors for unlocking devices. This feature not only provides security but also enhances convenience. You can simply touch the sensor to access your phone, making it quick and efficient. Fingerprint scanners are also used in various sectors, including banking and law enforcement. They help streamline processes and reduce the risk of fraud. Have you ever thought about how much time you save by using your fingerprint instead of remembering a complex password?
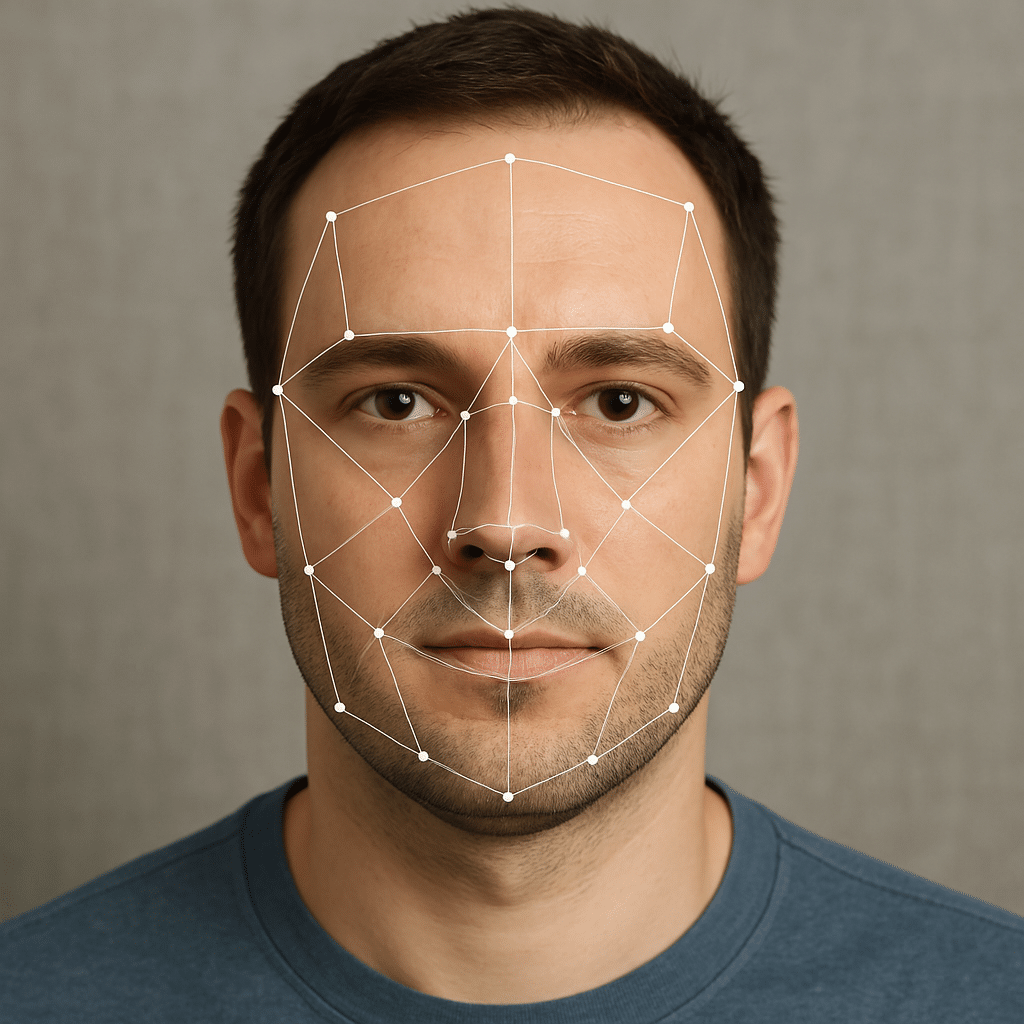
Facial Recognition Technology
Facial recognition technology has gained popularity due to its effectiveness and ease of use. This method analyzes facial features and compares them to stored images in a database. It can identify individuals in a matter of seconds. You may have noticed this technology when using social media platforms that automatically tag friends in photos. This not only makes sharing memories easier but also demonstrates the capability of facial recognition in everyday life. However, the use of facial recognition raises questions about privacy and ethics. Are you comfortable with how your facial data is being used? Understanding these implications is essential as we navigate this technology.
Voice Authentication
Voice authentication is a biometric solution that verifies identity through unique voice patterns, commonly used in customer service and banking to simplify the verification process and enhance security. While it offers a reliable option due to the difficulty of replicating voice patterns, factors like background noise or illness can affect its accuracy. As biometric technologies evolve, understanding their benefits and risks is crucial for the future of secure and convenient individual verification.
Online Verification Techniques
Online verification techniques ensure that individuals are who they claim to be. These methods enhance security and trust in various online interactions. They play a vital role in reducing fraud. Let’s explore some common techniques used today.
Digital Document Verification
Digital document verification checks the authenticity of online documents. This process often includes scanning IDs, passports, or other official papers. Advanced software can analyze these documents. It looks for signs of tampering or forgery. Many organizations use this technique to verify a person’s identity quickly and accurately.

E-signature Validation
E-signature validation confirms the identity of a signer in digital transactions. This method uses cryptographic methods to secure signatures. It ensures that the signature belongs to the person who signed it. Businesses rely on e-signatures for contracts and agreements. This technique speeds up processes while maintaining security.
Email And Phone Verification
Email and phone verification involve confirming contact information. Users receive a code via email or text message. They must enter this code to prove ownership. This method adds an extra layer of security. It helps prevent unauthorized access to accounts and personal data.
The Role Of Third-party Verification Services
Third-party verification services play a crucial role in individual verification. They help confirm a person’s identity through various methods, ensuring security and trust. This process is vital for businesses and institutions that require accurate identity checks for transactions and services.
Third-party verification services play a crucial role in individual verification processes. These services act as intermediaries, ensuring that the information provided about a person is accurate and trustworthy. By using a reliable third-party service, businesses can enhance their security measures, reduce fraud, and build trust with their customers.
Selecting A Trustworthy Service
Choosing the right third-party verification service can feel overwhelming. You want a service that is not only effective but also trustworthy. Look for services with positive reviews and a solid reputation in the industry. Consider the following factors when selecting a service:
- Experience:How long has the service been operating?
- Compliance:Does it adhere to local and international regulations?
- Technology:What methods does it use for verification? Biometric checks? Database searches?
Reach out to peers or colleagues for recommendations. Your personal network can often point you toward reliable options based on their experiences.
Understanding Data Privacy Implications
Data privacy is a significant concern when using third-party verification services. You must ensure that your personal information is handled securely and transparently. Before you proceed, ask yourself these questions:
- What data will the service collect?
- How will they use this information?
- Are they compliant with data protection laws like GDPR or CCPA?
It’s wise to read the service’s privacy policy. This document outlines how your data will be stored, shared, and protected. Your verification process should never compromise your privacy. Choose a service that prioritizes data security and offers clear communication about their practices. Navigating the world of individual verification can be complex, but understanding the role of third-party services and their implications can empower you to make informed decisions.
Government And Legal Frameworks
Government and legal frameworks play a crucial role in individual verification. These systems help ensure safety and compliance. They set rules and standards for verifying identities. Various programs and regulations guide businesses and organizations. Understanding these frameworks is vital for proper verification processes.
E-verify Program
The E-Verify program helps employers confirm employee work eligibility. It checks information against government records. Employers submit details to verify identity and employment status. The system speeds up the hiring process. It reduces the chance of hiring unauthorized workers. E-Verify is a voluntary program for most employers. However, some states require its use. It is an essential tool for compliance with immigration laws.
Anti-money Laundering (aml) Regulations
Anti-Money Laundering regulations aim to prevent financial crimes. They require businesses to verify the identity of customers. This helps stop illegal activities like money laundering. Financial institutions must implement strict verification processes. They monitor transactions to detect suspicious activities. Compliance with AML regulations is mandatory. Failure to comply can lead to severe penalties.
Know Your Customer (KYC) Compliance
Knowing your Customer compliance is crucial for financial businesses. KYC ensures companies know their clients’ identities. This process includes verifying personal information. KYC helps prevent fraud and financial crime. Businesses gather information like names and addresses. They may also check identification documents. KYC is essential for maintaining trust and safety in financial transactions.
Verification For The Individual User
Individual verification is essential for personal security. It helps confirm a person’s identity. This process protects users from fraud. Understanding how to verify your identity is crucial. It builds trust in online interactions.
Personal Preparedness And Awareness
Being prepared is key in the verification process. Know the types of information required. Common documents include IDs or utility bills. Always keep these documents updated.
Awareness of potential threats matters. Cyber threats are real and can affect anyone. Learn to recognize phishing attempts. Be cautious with personal information online.
Controlling Digital Identity
Take charge of your digital identity. Regularly check your online accounts. Use strong passwords and change them often. Enable two-factor authentication for extra security.
Monitor your digital footprint. Search for your name online. Remove outdated or incorrect information. This control helps maintain your reputation.
Stay informed about privacy settings. Adjust them on social media and other platforms. Understand what data you share and with whom.
Future Of Verification Technologies
The future of verification technologies is bright and full of promise. As the digital world grows, the need for secure identity verification becomes more critical. New technologies aim to make this process faster and safer. This evolution will shape how we verify identities in various sectors.
Innovations will focus on enhancing user experience while maintaining security. Technologies like AI, blockchain, and NFC will play a big role. Each of these advancements offers unique benefits for identity verification.
Ai And Machine Learning Innovations
AI and machine learning are changing the verification landscape. These technologies can analyze data patterns quickly. They help identify fraudulent activities in real-time.
AI systems learn from past verification attempts. This learning improves accuracy over time. Users benefit from a smoother experience with fewer verification hurdles.
Blockchain For Secure Identity Management
Blockchain technology provides a secure way to manage identities. It creates tamper-proof records that enhance trust. Each identity is stored in a decentralized manner.
This reduces the risk of data breaches. Users have more control over their personal information. Blockchain can simplify verification processes across various industries.
The Potential Of Nfc In Identity Verification
NFC, or Near Field Communication, offers quick verification solutions. Users can tap their devices for instant identity checks. This method enhances convenience and speed.
NFC technology also supports biometric verification. Fingerprints or facial recognition can be combined for added security. This integration makes identity verification seamless and efficient.
Frequently Asked Questions about Individutal Verification
What Is Individual Verification?
Individual verification is the process of confirming the identity of a single person. It involves methods like document checks, biometric scans, and knowledge-based authentication. This ensures accurate identification for various purposes, including security and compliance. Individual verification is essential for preventing fraud and protecting sensitive information.
How Do You Verify An Individual?
To verify an individual, utilize methods like knowledge-based authentication, two-factor authentication, and biometric verification. Collect government-issued IDs, check credit bureau data, and employ online verification tools. These approaches ensure a reliable and secure identity verification process.
What Are The Two Types Of Verification?
The two types of verification are double entry and proofreading. Double entry involves entering data twice and comparing the results. Proofreading requires checking the entered data against the original document for accuracy. These methods ensure data integrity and minimize errors.
What Are The Three Methods To Verify An Individual’s Identity?
Three methods to verify an individual’s identity are: 1. Government-issued photo identification. 2. Credit file checks. 3. Biometric verification methods. These approaches ensure accurate identity confirmation and enhance security measures.
Conclusion
Individual verification is essential in today’s world. It builds trust and security. Effective methods include biometric checks and two-factor authentication. Each method has its benefits and can suit different needs. Understanding these options helps you choose the right one. Always prioritize your personal data protection.
With the right approach, verifying identities becomes easier and safer. Stay informed and make smart choices for your security. Take the necessary steps to ensure your identity is verified correctly. This protects you and enhances your online experience.


https://flerus-shop.hcp.dilhost.ru/club/user/73/blog/359/