Presentation Attack Detection (PAD) identifies fraudulent attempts to deceive biometric systems. It ensures security by detecting fake inputs like masks or photos.
In today’s digital age, biometric authentication has become crucial for security. Despite its advantages, it faces threats from presentation attacks, where impostors use fake artifacts to trick systems. PAD technology combats these threats by distinguishing between genuine and fake inputs.
It employs advanced algorithms and sensors to analyze physical and behavioral traits. Effective PAD enhances the reliability of biometric systems, safeguarding sensitive data and access points. Organizations must integrate PAD into their security measures to ensure robust protection against evolving cyber threats. Investing in PAD technology is essential for maintaining trust and integrity in biometric authentication systems.
Introduction To Presentation Attack Detection
Presentation Attack Detection (PAD) is crucial in biometric security. It helps identify fake biometric samples. These samples can trick biometric systems. PAD ensures that only genuine samples get access.
Importance Of Biometric Security
Biometric security uses unique traits like fingerprints and facial recognition. These traits are hard to fake. This makes biometric systems secure. They protect sensitive data and personal information.
Biometric security is used in:
- Smartphones
- Banking
- Healthcare
- Government IDs
Ensuring the safety of these systems is vital. Presentation Attack Detection plays a key role here.
Overview Of Presentation Attack Detection
Presentation attacks involve using fake biometric samples. These samples deceive the biometric system. Common types of attacks include:
- Spoofing: Using fake fingerprints or facial masks.
- Replay Attacks: Replaying recorded biometric data.
- Morphing: Creating a hybrid biometric sample.
These attacks can compromise security. Therefore, detecting them is essential.
A strong PAD system can detect these fake samples. It ensures that only real biometric data gets access.
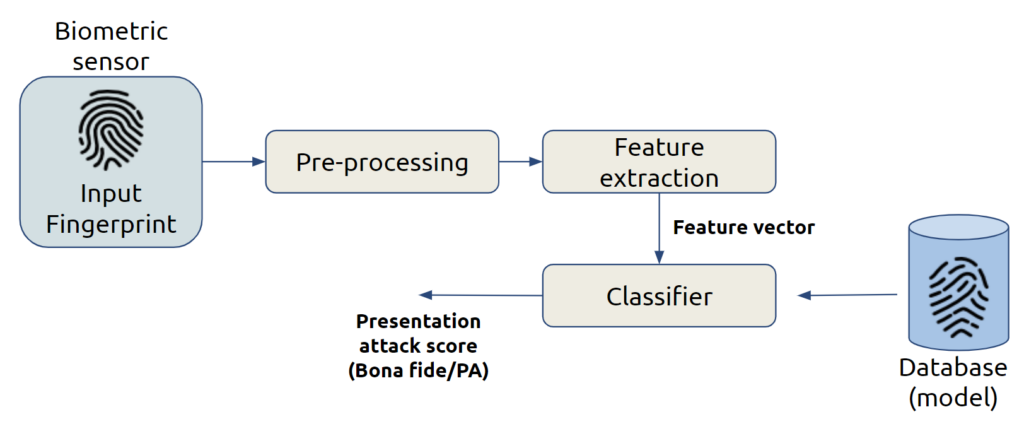
Types Of Presentation Attack Detection
Presentation attacks can trick biometric systems. They use fake traits to bypass security. Understanding the types of attacks helps improve security. Below are the main types of presentation attacks.
Spoofing Attacks
Spoofing attacks use fake biometrics to fool the system. Examples include:
- Fake fingerprints made of silicone.
- Photos or masks to mimic faces.
- Voice recordings to imitate someone’s voice.
Attackers use these methods to access secure areas. Preventing spoofing is crucial for safety.
Replay Attacks
Replay attacks involve using recorded biometric data. Attackers capture and reuse this data. For example:
- Recording a voice and playing it back.
- Using a video of someone’s face.
Replay attacks can be hard to detect. Strong encryption helps prevent these attacks.
Techniques For Presentation Attack Detection
Presentation attacks, also known as spoofing attacks, threaten biometric systems. Detecting these attacks is crucial for maintaining security. Various techniques can identify and prevent these threats. Below are some of the most effective methods.
Hardware-based Methods
Hardware-based methods involve special devices to detect presentation attacks. These devices often use sensors and cameras. The most common techniques include:
- Fingerprint Scanners: Advanced scanners can detect fake fingerprints.
- Facial Recognition Cameras: These cameras identify real faces from photos or masks.
- IR and UV Sensors: These sensors verify the authenticity of the biometric sample.
These methods rely on physical attributes and environmental conditions. They often provide high accuracy and reliability.
Software-based Methods
Software-based methods use algorithms and data analysis. These methods examine the biometric data for signs of spoofing. Common techniques include:
- Image Analysis: Software checks for inconsistencies in images.
- Behavioral Analysis: This method monitors user behavior patterns.
- Machine Learning: Algorithms learn to identify presentation attacks over time.
These methods can quickly adapt to new types of attacks. They are often used alongside hardware-based methods for better security.
| Method Type | Examples | Benefits |
| Hardware-Based | Fingerprint Scanners, Facial Recognition Cameras, IR Sensors | High Accuracy, Physical Verification |
| Software-Based | Image Analysis, Behavioral Analysis, Machine Learning | Adaptable, Quick Detection |
Combining these techniques can provide comprehensive security. Each method has its strengths and weaknesses. Using both hardware and software methods ensures robust protection against presentation attacks.
Biometric Modalities And Vulnerabilities in Presentation Attack Detection
Presentation Attack Detection (PAD) is essential in biometric systems. It ensures the authenticity of the user. Various biometric modalities, like fingerprints and facial recognition, are used. Each modality has its own vulnerabilities. Understanding these is crucial for improving security.
Fingerprint Recognition
Fingerprint recognition is a common biometric modality. It scans the unique patterns on a finger. Yet, it has vulnerabilities that attackers exploit.
- Fake fingerprints can bypass the system.
- Attackers use materials like silicone or gelatin.
- Older sensors struggle with these fake prints.
Advanced sensors with liveness detection are better. They check for signs of a real finger. These include sweat and blood flow. Improving these sensors reduces attacks.
Facial Recognition
Facial recognition uses the unique features of a face. It matches these features with stored data. But, it also has vulnerabilities.
- Attackers use photos or videos to trick the system.
- 3D masks are another method.
- Lighting conditions can affect accuracy.
Advanced systems use 3D imaging and infrared sensors. These technologies detect depth and heat. They help in identifying fake faces and improve security.
| Biometric Modality | Common Vulnerabilities | Advanced Solutions |
| Fingerprint Recognition | Fake fingerprints with silicone or gelatin | Liveness detection with sweat and blood flow |
| Facial Recognition | Photos, videos, 3D masks | 3D imaging, infrared sensors |
Challenges In Presentation Attack Detection
Presentation Attack Detection (PAD) is vital for security systems. Yet, it faces many challenges. These challenges affect the system’s performance and reliability.
Accuracy Issues
Accuracy is crucial in PAD systems. False positives and false negatives can occur. False positives mean the system detects a threat when there is none. False negatives mean the system misses an actual threat. Both are problematic and reduce trust in the system.
Different environments impact accuracy. Changes in light or camera quality affect detection. These inconsistencies make the system less reliable.
User Convenience
User convenience is another challenge. High security often means complex procedures. Users want quick and easy access. Complex PAD systems can slow down access and frustrate users.
The balance between security and convenience is hard to achieve. Too much security can make the system hard to use. Too little can make it vulnerable to attacks.
Advancements In Detection Technologies
Advancements in Detection Technologies have significantly enhanced our ability to counter presentation attacks. These technologies help secure biometric systems by ensuring the authenticity of users. Let’s explore some of the key advancements that have revolutionized this field.
Machine Learning Approaches
Machine learning has brought a new dimension to Presentation Attack Detection (PAD). These approaches use algorithms to identify patterns and anomalies. They can differentiate between real and fake biometric data.
There are several machine learning techniques used in PAD:
- Supervised Learning: Uses labeled data to train models.
- Unsupervised Learning: Identifies hidden patterns in unlabeled data.
- Deep Learning: Utilizes neural networks for complex pattern recognition.
These techniques improve the accuracy and reliability of PAD systems. They learn from data and constantly evolve, enhancing security over time.
Multimodal Biometric Systems
Multimodal biometric systems combine multiple biometric traits. This makes attacks more difficult and detection more accurate. These systems use a combination of fingerprints, facial recognition, and voice recognition.
Advantages of multimodal systems include:
- Higher security through multiple verification methods.
- Improved accuracy by reducing false acceptance rates.
- Increased user convenience with multiple biometric options.
| Biometric Trait | Strength | Weakness |
| Fingerprint | High uniqueness | Vulnerable to fake prints |
| Facial Recognition | Non-intrusive | Can be spoofed with photos |
| Voice Recognition | Convenient | Background noise issues |
By combining these traits, multimodal systems provide a robust defense against presentation attacks. They ensure a higher level of security and user trust.
Case Studies And Real-world Applications
Case Studies and Real-World Applications of Presentation Attack Detection (PAD) highlight its importance in various sectors. This section delves into specific industries, showcasing how PAD technology safeguards against fraud and unauthorized access.
Banking And Financial Services
The banking sector faces numerous security threats. PAD technology plays a crucial role in protecting financial transactions. Biometric authentication methods like facial recognition and fingerprint scanning are common in banks.
Consider a major bank that implemented PAD solutions. This bank reduced identity fraud by 30% within a year. PAD systems can detect fake identities and presentation attacks, ensuring customer security.
In another case, a financial services company integrated PAD with their mobile app. This integration prevented unauthorized access, safeguarding sensitive customer data. The company reported a significant drop in fraudulent activities.
| Bank | Year of Implementation | Fraud Reduction |
| ABC Bank | 2021 | 30% |
| XYZ Financial | 2022 | 40% |
Border Security
Border security agencies also benefit from PAD technology. Biometric systems at border checkpoints require robust PAD measures to prevent illegal entry.
One border security agency integrated PAD into their facial recognition systems. This helped identify individuals using masks or photos to spoof identity checks. The agency reported a 25% increase in detection of illegal entries.
Another case study involves an airport that adopted PAD for their e-gates. These gates verify passenger identities quickly while ensuring high security. PAD technology here detected false representations, enhancing overall safety.
Key benefits of PAD in border security include:
- Enhanced identity verification
- Reduced illegal entries
- Quick and secure passenger processing
Real-world applications of PAD demonstrate its effectiveness and necessity across various industries. Whether in banking or border security, PAD technology ensures a safer and more secure environment.
Future Directions In Biometric Security
Biometric security is evolving rapidly. Presentation Attack Detection (PAD) is critical. Future directions in biometric security explore new technologies and policies. These advancements promise enhanced security and user convenience.
Emerging Technologies
New technologies are shaping the future of biometric security. Artificial Intelligence (AI) plays a significant role in improving PAD systems. AI can detect subtle differences in biometric data. This helps in identifying fake presentations more effectively.
Machine Learning (ML) algorithms are also crucial. They can analyze vast amounts of biometric data. This helps in training systems to recognize genuine users accurately. Deep Learning techniques further enhance this capability.
3D Imaging is another emerging technology. It provides more detailed biometric data. This makes it harder for attackers to replicate genuine biometric traits. Multimodal Biometrics combines multiple biometric modalities. This adds an extra layer of security.
| Technology | Advantage |
| Artificial Intelligence (AI) | Improves detection accuracy |
| Machine Learning (ML) | Analyzes large data sets |
| 3D Imaging | Provides detailed biometric data |
| Multimodal Biometrics | Enhances security layers |
Policy And Regulation
Policy and regulation are essential for biometric security. Governments are creating guidelines for biometric data use. These policies ensure data privacy and protection. They also set standards for PAD systems.
Regulations require companies to follow strict protocols. This includes regular audits and compliance checks. Data protection laws ensure that personal data is not misused. They mandate secure storage and processing of biometric data.
International standards are also being developed. These standards facilitate global cooperation. They ensure that PAD systems are effective worldwide. Organizations must stay updated with these regulations. This ensures their biometric systems remain compliant.
Frequently Asked Questions
What Is Face Presentation Attack Detection?
Face presentation attack detection identifies fake faces used to deceive facial recognition systems. It ensures security by detecting spoofing attempts. This technology protects against fraud by recognizing masks, photos, and videos.
What Is A Presentation Attack?
A presentation attack is an attempt to deceive biometric systems using fake samples, like masks or fingerprints, to gain unauthorized access.
Which Attacks Are Forms Of Presentation Attacks?
Presentation attacks include spoofing, where fake biometrics are used, and replay attacks, where recorded data is replayed. These methods deceive biometric systems.
What Is Attack Detection?
Attack detection identifies and monitors suspicious activities in a system or network. It helps prevent security breaches.
What Is Presentation Attack Detection?
Presentation attack detection refers to techniques used to identify and prevent spoofing attempts on biometric systems.
Why Is Presentation Attack Detection Important?
It ensures the security and integrity of biometric authentication systems by preventing unauthorized access.
How Does Presentation Attack Detection Work?
It uses algorithms and sensors to differentiate between genuine biometric traits and fake ones like photos or masks.
What Are Common Presentation Attack Detection Methods?
Common methods include using photos, videos, masks, or even 3D printed models to spoof biometric systems.
Conclusion
Protecting against presentation attacks is crucial for secure authentication. Implementing effective detection methods ensures system integrity. Stay informed about evolving threats and invest in advanced technologies. By prioritizing security, you can safeguard sensitive information and maintain trust. Always remain vigilant and proactive in enhancing your defense mechanisms.

