Online identity authentication technology verifies a user’s identity before granting access to systems or services. It ensures secure transactions and protects sensitive data.
Online identity authentication technology is crucial in today’s digital age. It helps prevent unauthorized access to personal and financial information. Methods like biometrics, multi-factor authentication, and secure tokens enhance security. These technologies reduce the risk of identity theft and cyberattacks.
Companies and individuals benefit from improved trust and safety. With increasing online transactions, robust authentication methods are essential. They provide peace of mind by safeguarding sensitive data. Investing in advanced authentication technologies is vital for maintaining digital security. Reliable identity verification fosters a secure online environment for all users.
Introduction To Online Identity Authentication
In the digital age, verifying online identities is crucial. Online identity authentication ensures that users are who they claim to be. This process protects sensitive data and prevents unauthorized access. It also builds trust between users and online services.
Importance Of Secure Access
Secure access is vital for protecting personal and financial information. Unauthorized access can lead to identity theft and data breaches.
Key benefits of secure access include:
- Protecting sensitive information from cybercriminals
- Ensuring only authorized users access the data
- Building trust between service providers and users
Historical Context
In the early internet days, simple passwords were enough for security. As online threats grew, multi-factor authentication (MFA) became necessary. MFA uses multiple verification methods, like passwords and biometrics.
Here is a brief timeline of online identity authentication development:
| Year | Milestone |
| 1990s | Introduction of basic passwords for online accounts |
| 2000s | Emergence of multi-factor authentication (MFA) |
| 2010s | Adoption of biometrics like fingerprints and facial recognition |
| 2020s | Widespread use of advanced AI and machine learning for authentication |
Over time, online identity authentication has evolved. It continues to adapt to emerging threats and technologies.
Types Of Authentication Methods
Online identity authentication is crucial today. Different methods ensure secure access. Here, we explore two common methods: password-based and biometric authentication.
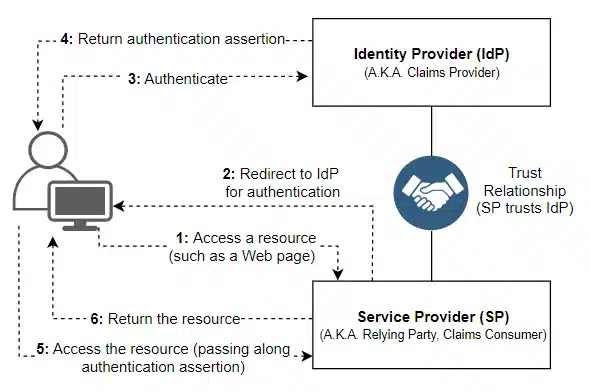
Password-based Authentication
Password-based authentication is widely used. Users create a password to access their accounts. This method is simple but requires strong password policies.
Key features of password-based authentication:
- Easy to implement
- Requires user-created passwords
- Can be combined with other methods for added security
Best practices for passwords include:
- Use a mix of letters, numbers, and symbols
- Avoid common words and phrases
- Change passwords regularly
Biometric Authentication
Biometric authentication uses unique physical traits. Examples include fingerprints, facial recognition, and iris scans. This method is more secure than passwords.
Advantages of biometric authentication:
- Harder to fake or steal
- Does not rely on user memory
- Quick and convenient
Common types of biometric authentication include:
| Type | Description |
| Fingerprint | Uses unique patterns of fingerprints |
| Facial Recognition | Scans facial features for identity |
| Iris Scan | Examines unique patterns in the iris |
Multi-factor Authentication
Multi-Factor Authentication (MFA) is a security technology. It uses multiple verification steps to authenticate users. This method enhances security by requiring more than one form of identification. Let’s dive deeper into what MFA is and its benefits.
What Is Mfa?
Multi-Factor Authentication (MFA) adds extra layers of protection. It requires users to provide two or more verification factors. These factors can be something you know, something you have, or something you are.
- Something you know: A password or PIN.
- Something you have: A smartphone or security token.
- Something you are: Fingerprint or facial recognition.
Benefits Of Mfa
MFA offers several advantages for securing online identities. Here are some key benefits:
| Benefit | Description |
| Enhanced Security | MFA reduces the risk of unauthorized access. Even if one factor is compromised, others remain secure. |
| Compliance | MFA helps meet regulatory requirements. Many industries demand strong authentication methods. |
| User Confidence | MFA increases user trust in the platform. Users feel safer knowing extra security measures are in place. |
| Reduced Fraud | MFA makes it harder for attackers to steal identities. This reduces the chance of fraud. |
Implementing MFA is simple and highly effective. It significantly boosts security and user trust.
Biometric Authentication Technologies
Biometric authentication technologies are changing how we verify identities online. These technologies use unique physical traits. They ensure secure and quick access to systems. Below, we explore two popular methods: fingerprint scanning and facial recognition.
Fingerprint Scanning
Fingerprint scanning is a common biometric method. Each person’s fingerprint is unique. This makes it a secure way to verify identity. The scanner captures the fingerprint pattern. It compares the pattern to stored data.
Here are some benefits of fingerprint scanning:
- High Accuracy: Unique patterns reduce the risk of false matches.
- Convenience: Quick and easy to use.
- Security: Difficult to fake or steal fingerprints.
Fingerprint scanners are used in many devices. Smartphones, laptops, and security systems often have them. This technology is reliable and trusted by many.
Facial Recognition
Facial recognition is another popular biometric method. It analyzes unique facial features. This includes the distance between eyes, nose shape, and jawline. A camera captures the user’s face. The system then compares it to the stored data.
Here are some benefits of facial recognition:
- Non-Intrusive: Users do not need to touch any device.
- Speed: Quickly verifies identity in seconds.
- Versatility: Works in various lighting conditions.
Facial recognition is widely used in security systems. Airports, offices, and smartphones use this technology. It provides a seamless and secure user experience.
Behavioral Biometrics
Behavioral biometrics is a cutting-edge field in online identity authentication. It uses unique behavioral patterns to verify identities. This technology focuses on how a user interacts with devices. Let’s explore two important aspects of behavioral biometrics.
Keystroke Dynamics
Keystroke dynamics analyzes the way a person types on a keyboard. It records the rhythm and speed of typing. Each person has a unique typing pattern. This makes keystroke dynamics a strong authentication method.
Some key features of keystroke dynamics include:
- Typing Speed: Measures how fast a user types.
- Key Hold Time: Tracks the time each key is pressed.
- Flight Time: Records the time between key presses.
Mouse Movement Patterns
Mouse movement patterns involve tracking how a user moves the mouse. These patterns include speed, direction, and click frequency. Every user has a unique way of moving the mouse. This makes it an effective tool for identity verification.
Key elements of mouse movement patterns are:
- Pointer Speed: Measures how fast the mouse pointer moves.
- Click Patterns: Tracks the frequency and location of clicks.
- Trajectory: Observes the path the mouse takes.
Authentication In Mobile Devices
Mobile devices have transformed the way we authenticate our identities. Advanced technologies now allow secure and easy access. Let’s explore some key methods used in mobile authentication.
Fingerprint Sensors
Fingerprint sensors are common in mobile devices today. They provide a quick and reliable way to unlock phones. Users can register their fingerprints in the device settings. The sensor then matches the fingerprint with the stored data.
Fingerprint sensors offer several benefits:
- Fast and convenient
- High level of security
- Less prone to hacking
But, they do have some limitations. Dirty or wet fingers can cause issues. Additionally, the sensor can wear out over time.
Face Id And Iris Scanning
Face ID and iris scanning are newer technologies in mobile devices. They use the unique features of a user’s face or eyes for authentication. Face ID uses the front camera to scan the user’s face. Iris scanning uses infrared light to capture the eye’s unique patterns.
These methods offer:
- Hands-free access
- High accuracy
- Enhanced security
Face ID and iris scanning are very secure. They can recognize the user even with changes in appearance.
However, they also have drawbacks. Poor lighting can affect their performance. Users must look directly at the device for it to work. Despite these issues, these technologies continue to improve and become more reliable.
Blockchain For Identity Verification
Blockchain technology is changing the way we verify identities online. It offers a secure and decentralized method. This ensures personal data remains private and tamper-proof.
How Blockchain Works
Blockchain is a system of recording information. It makes it hard to change or hack the system. A blockchain is a digital ledger of transactions. These transactions are duplicated and distributed across the entire network of computer systems on the blockchain.
Each block in the chain contains a number of transactions. Every time a new transaction occurs, a record of that transaction is added to every participant’s ledger. The decentralized database managed by multiple participants is known as Distributed Ledger Technology (DLT).
Advantages Of Blockchain
| Advantage | Description |
| Security | Blockchain uses cryptographic algorithms to secure data. This ensures that data is tamper-proof. |
| Transparency | All transactions are transparent. Anyone can verify them. |
| Decentralization | No single entity controls the blockchain. This reduces the risk of data breaches. |
| Efficiency | Blockchain can streamline identity verification processes. This makes them faster and more efficient. |
Artificial Intelligence In Authentication
Artificial Intelligence (AI) is revolutionizing online identity authentication. It adds a layer of security. This technology uses advanced algorithms. These algorithms verify users quickly and accurately. AI makes the authentication process seamless and secure.
Ai-powered Fraud Detection
AI-powered fraud detection is critical in online authentication. It analyzes user behavior. It identifies unusual patterns. This technology can detect fraud in real-time. It reduces the risk of unauthorized access.
- Behavior Analysis: AI monitors user behavior. It learns their routines. It detects deviations from normal activities.
- Real-Time Detection: AI identifies suspicious activities instantly. It flags potential fraud quickly.
- Adaptive Learning: AI systems adapt over time. They get better at spotting fraud.
Machine Learning Algorithms
Machine learning algorithms play a key role in authentication. These algorithms learn from data. They improve over time. They make the authentication process smarter.
| Algorithm | Function |
| Decision Trees | Classify data into categories. Useful for binary decisions. |
| Neural Networks | Mimic human brain function. Handle complex data patterns. |
| Random Forest | Combine multiple decision trees. Improve accuracy. |
Machine learning algorithms provide robust security. They can handle large amounts of data. They improve as they process more information.
- Data Collection: Gather data from user interactions.
- Pattern Recognition: Identify patterns in the data.
- Continuous Improvement: Enhance accuracy through continuous learning.
Challenges In Online Identity Authentication
Online identity authentication is crucial in today’s digital world. However, it comes with several challenges. These challenges can threaten the security and privacy of users. Let’s explore some of these challenges.
Security Breaches
Security breaches are a significant concern in online identity authentication. Hackers constantly look for vulnerabilities. They use these weaknesses to gain unauthorized access. This can result in stolen personal information.
There are various methods hackers use, such as:
- Phishing attacks
- Malware
- Man-in-the-middle attacks
Organizations must stay vigilant. They need to update their security measures regularly. This helps in minimizing the risk of security breaches.
User Privacy Concerns
User privacy is another significant challenge. Many users worry about how their data is used. They fear that their personal information might be misused.
Companies must be transparent about their data collection methods. They should inform users how their data is stored and used. This helps build trust with the users.
Here are some common privacy concerns:
- Unauthorized data sharing
- Lack of data encryption
- Inadequate privacy policies
Addressing these concerns is crucial for maintaining user trust. It also helps in ensuring compliance with data protection laws.
Regulatory Compliance
Online identity authentication technology must comply with various regulations. These regulations ensure data protection and user privacy. Non-compliance can lead to penalties or legal issues. Companies must stay updated with these regulations.
Gdpr And Data Protection
The General Data Protection Regulation (GDPR) is a critical law. It protects the data of EU citizens. Companies must handle data with care. They need explicit consent to collect user data. They must also ensure data is stored securely.
GDPR also gives users rights over their data. Users can request data deletion or access. Companies need to comply with these requests promptly. This regulation ensures users feel safe online.
Here’s a quick overview of GDPR requirements:
- Explicit user consent for data collection
- Secure data storage practices
- User rights to access and delete data
- Regular data protection audits
Industry Standards
Industry standards are essential for online identity authentication. They ensure consistent and secure practices. Following these standards can prevent data breaches. It also builds user trust.
Some key industry standards include:
- ISO/IEC 27001: Information Security Management
- PCI-DSS: Payment Card Industry Data Security Standard
- NIST: National Institute of Standards and Technology guidelines
Adhering to these standards involves regular audits. Companies must also update their security measures. This ensures they meet the latest security requirements.
Implementing these standards can be complex. Companies often use specialized software for compliance. This software helps automate compliance processes.
Below is a comparison of key industry standards:
| Standard | Focus Area | Key Requirement |
| ISO/IEC 27001 | Information Security | Risk Management |
| PCI-DSS | Payment Data | Encryption and Monitoring |
| NIST | General Security | Security Controls |
Meeting these standards is crucial. It ensures the safety and security of user data. It also helps in maintaining a company’s reputation.
Future Trends In Identity Authentication Technology
The future of online identity authentication is evolving rapidly. New technologies ensure higher security and better user experience. These trends aim to protect digital identities more effectively.
Advancements In Biometric Tech
Biometric technology is becoming more advanced and reliable. It’s not just about fingerprints anymore. Facial recognition and iris scanning are gaining popularity.
Here are some key advancements:
- Enhanced accuracy: Modern algorithms reduce errors significantly.
- Speed: Biometric scans are faster than ever.
- Multimodal biometrics: Combines multiple types like fingerprint and face.
These advancements make biometric authentication more secure and user-friendly.
Emerging Authentication Methods
New methods of authentication are emerging to complement traditional ones. They focus on reducing reliance on passwords.
Some of the emerging methods include:
| Method | Description |
| Behavioral Biometrics | Analyzes user behavior like typing speed and mouse movements. |
| Token-Based Authentication | Uses physical tokens or devices to verify identity. |
| Zero-Knowledge Proof | Proves identity without revealing sensitive information. |
These methods offer more flexibility and security. They aim to make authentication seamless and robust.
Case Studies
Online identity authentication technology has transformed digital security. Understanding its real-world applications helps in grasping its impact. Below, we explore key case studies showcasing successful implementations and lessons learned.
Successful Implementations
Several companies have successfully implemented online identity authentication. Here are a few standout examples:
- Bank of America: They use biometric authentication for secure banking. This includes fingerprint and facial recognition.
- Amazon: Multi-factor authentication secures user accounts. This has reduced unauthorized access significantly.
- PayPal: They use advanced AI to detect fraudulent activities. This helps in safeguarding user transactions.
The table below summarizes the key benefits observed:
| Company | Technology Used | Key Benefits |
| Bank of America | Biometric Authentication | Enhanced Security, User Convenience |
| Amazon | Multi-factor Authentication | Reduced Unauthorized Access |
| PayPal | AI Fraud Detection | Safeguarded Transactions |
Lessons Learned
Implementing online identity authentication isn’t without challenges. Here are some lessons learned from various implementations:
- User Education: Users must understand the importance of security features. Companies should provide clear instructions and support.
- Regular Updates: Technology evolves quickly. Regular updates ensure that security measures remain effective.
- Balancing Security and Convenience: Too many security layers can frustrate users. Finding the right balance is crucial.
These lessons help in refining the authentication process. Continuous improvement ensures better security and user experience.
Best Practices For Secure Identity Authentication
Secure authentication is vital for protecting online identities. Adopting best practices ensures robust security and minimizes risks. Below are key strategies to enhance online identity authentication technology.
Strong Password Policies
Implementing strong password policies is crucial for secure authentication. Ensure passwords are complex and unique. This reduces the chances of unauthorized access.
Encourage users to create passwords that include:
- At least 12 characters
- A mix of uppercase and lowercase letters
- Numbers and special characters
Require users to change their passwords regularly. Enforce policies that prevent the reuse of old passwords. Strong passwords are the first line of defense against cyber threats.
Regular Security Audits
Conducting regular security audits is essential for maintaining secure authentication systems. Audits help identify vulnerabilities and ensure compliance with security standards.
During audits, review the following:
| Aspect | Importance |
| Password policies | Ensure they are enforced and updated |
| Access logs | Check for suspicious activities |
| Software updates | Verify all systems are up-to-date |
Document findings and implement necessary improvements promptly. Regular audits help maintain a high level of security and user trust.
Frequently Asked Questions
What Is Online Identity Authentication?
Online identity authentication verifies a user’s identity through digital methods. It ensures that the person accessing services is who they claim to be. This process often involves passwords, biometrics, or multi-factor authentication.
How Does Online Identity Authentication Work?
Online identity authentication uses various methods to confirm user identities. These methods include passwords, biometrics, and multi-factor authentication. Each step adds a layer of security.
Why Is Online Identity Authentication Important?
Online identity authentication is crucial for security. It protects sensitive information from unauthorized access. This process also helps prevent identity theft and fraud.
What Are Common Methods Of Identity Authentication?
Common methods include passwords, biometrics, and multi-factor authentication. Passwords are the most basic. Biometrics use unique physical traits. Multi-factor requires multiple verification steps.
Conclusion
Online identity authentication technology is crucial for secure digital interactions. It helps protect personal data and prevents fraud. Businesses and individuals must adopt these tools. Embracing advanced authentication methods ensures safer online experiences. Stay ahead by prioritizing robust security measures in your digital activities.


One Reply on “Top 3 Online Identity Authentication Technology: Ensuring Secure Access”